Protecting the IoT environment from cybercriminals, everything is a computer today. A microwave is a computer that heats things. A refrigerator is a computer that keeps things cold.
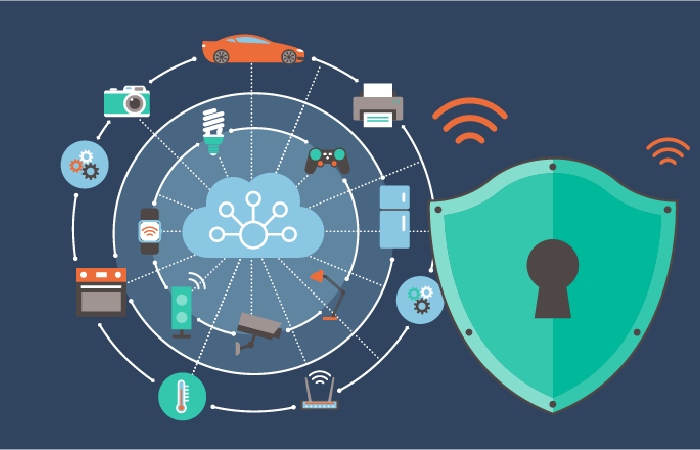
A Smartphone is a small computer that makes phone calls. ATMs are computers that contain money. These computing devices are everywhere in our daily lives.
And also, thanks to the advent of low-cost microcomputer chips and wireless networks, almost anything (physical) can connect to the web for remote management of IoT devices.
As everything becomes a computer, computer security becomes more and more critical. In cyberspace, cybercriminals scan and compromise IoT devices and use them for malicious activities.
The privacyenbescherming internet security system is a collection of technologies that defend an organization against cyber criminals attempting to steal data, money or identities by accessing the organization’s network, browsers, operating system and application through the internet.
What is being targeted in the IoT environment?
Targeted IoT devices include connected medical devices, routers, smart refrigerators, smart fire alarms, streaming devices, IP cameras, smart security systems, network-attached storage devices, and more. Cybercriminals are now very active and are constantly scanning for unprotected IoT devices. The dramatic increase in port scans is ample evidence.
What is the risk?
However, Hackers use compromised IoT devices to cause havoc within IoT networks. These harmful activities include:
- Sending spam mail
- Obfuscation of network traffic
- Internet browsing masking
- Click fraud generation
- Perform credential stuffing attacks (use automated scripts to test stolen credentials from other data breach incidents)
- Selling IoT botnets to other cybercriminals for profit
What if your resolution for 2023 was to better secure your Internet surfing? It all starts with the use of a lesmeilleursvpn (or virtual private network). It must be said that lesmeilleursvpn has many advantages by allowing you to access blocked or censored sites, to download serenely, to unblock foreign streaming platforms or even to make good savings when shopping. Moreover, our cyber security experts have vetted the major VPN providers by analyzing speed, security, and respect for your privacy.
IoT device protection

IoT devices make our lives more comfortable. However, most of them lack the security points common in computers, laptops, and smartphones.
Moreover, to protect your IoT devices from cybercriminals, we recommend:
- Change the default user name and password.
- Make sure your IoT device is up to date and has the latest security patches.
- Configure your firewall to allow traffic from trusted IP addresses and disable port forwarding.
- Before you get a new IoT device and take it home, you should always consider whether it benefits you.
- Use available security solutions.
The main issue here is that people have security solutions on laptops or PCs. Still, many other devices in the home or business are not safe, and most IoT devices cannot install security solutions. So what can you do about it?
And also, the best solution is to integrate security measures from your ISP. This appears in the MicroAI field. Based on the level of implementation determined by the ISP, users no longer have to worry about whether the IoT device is secure.
Moreover, MicroAI is developed to enable machine operators and device managers to collect specific data about their assets in real-time without relying on the cloud. The result is an increased awareness of operational performance and security.
This increased awareness leads to an acceleration of the digital conversion business. Besides, MicroAI can provide real-time critical alerts to those who need it most, making workers and their environments safer and more productive.
Conclusion
However, an overview shows the leading IoT environment security issues, focusing on the security challenges related to IoT devices and services. Security challenges such as confidentiality, data protection, and trust of the entity were identified.
Tech Support Reviews show that security and privacy challenges need to be addressed to establish more secure and more readily available IoT devices and services. The discussion also focused on cyber threats, including actors, motivation, and capacities driven by the unique properties of cyberspace.
And also found that threats from intelligence agencies and criminal groups are likely to be more difficult to ward off than those from individual hackers. This is because your targets can be much less predictable, while the effects of a single attack are likely to be less severe.





One Comment
[…] solution in any emergency. But not just that, VMware VM backups are an integral part of repelling cybercriminals. VMware backup software is equipped with many cyber threat prevention features to protect the VM […]